Hyperlane represents a fundamental shift in how blockchain networks communicate and interact. By introducing a permissionless deployment model combined with sophisticated security customization, Hyperlane enables developers to build cross-chain applications that maintain complete control over their security parameters. This approach eliminates the vulnerabilities inherent in traditional bridge designs while providing unprecedented flexibility for application-specific requirements.
What is Hyperlane? The Complete Guide to Modular Bridge Security
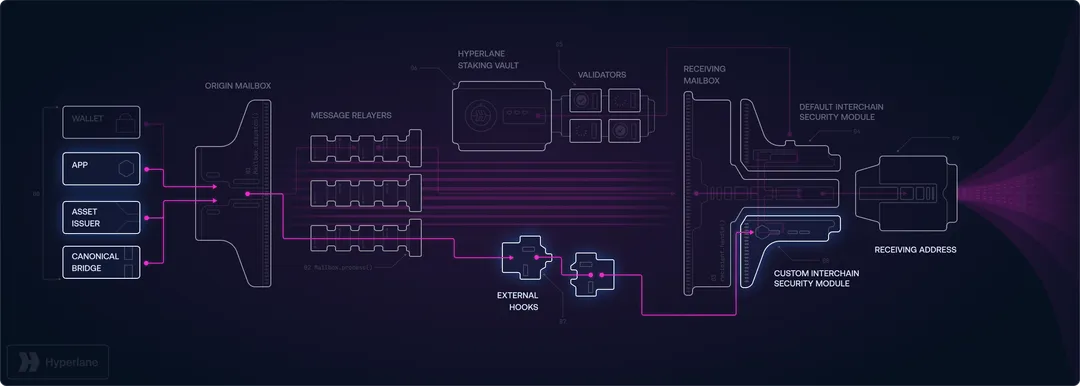
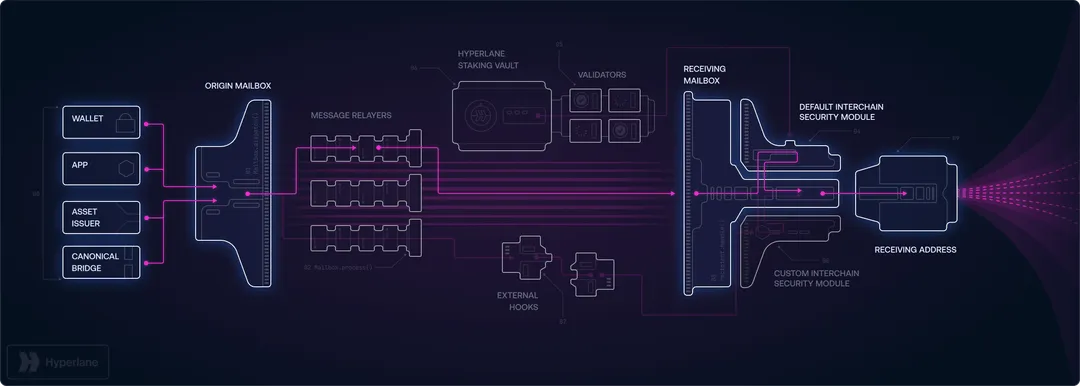
Hyperlane bridge is an open-source blockchain interoperability framework designed to connect various virtual machines (VMs), chains, and applications within the blockchain ecosystem. The Hyperlane infrastructure serves as a comprehensive system that facilitates seamless communication between different blockchain environments. The platform addresses critical limitations in existing cross-chain solutions by implementing a decentralized, permissionless architecture that allows any developer to establish secure messaging channels without requiring centralized approval or governance.
Traditional cross-chain security bridges operate under restrictive permission models that create bottlenecks and security vulnerabilities. Hyperlane revolutionizes this approach by enabling autonomous deployment of messaging contracts on any compatible blockchain. Unlike traditional bridges that use monolithic security models with centralized validator sets, Hyperlane implements a permissionless bridges deployment model with modular security. Developers can instantly establish connectivity between chains, virtual machines, and applications without waiting for approval from centralized authorities or validator committees.
The Hyperlane ecosystem provides a comprehensive toolkit for building secure multichain applications. Through innovative Interchain Security Modules (ISMs) and flexible deployment options, developers can create cross-chain solutions that match their specific risk profiles and operational requirements, ensuring optimal bridge security without compromising on functionality or performance.
Hyperlane's Core Innovation: Permissionless Interoperability
Hyperlane messaging operates on a fundamentally different principle than traditional bridges. Instead of requiring centralized approval, the platform's core messaging contract—known as the Mailbox—can be deployed autonomously by any developer on any supported blockchain. This permissionless bridges model eliminates gatekeepers and creates a truly decentralized blockchain interoperability layer that enhances cross-chain security.
Autonomous Deployment
Developers can deploy Hyperlane's messaging infrastructure independently on any blockchain without requiring permission or approval. This autonomous deployment capability ensures rapid connectivity establishment and eliminates bureaucratic delays that slow innovation in traditional bridge ecosystems.
Modular Security Architecture
Hyperlane's Interchain Security Modules (ISMs) provide granular control over security mechanisms. The modular security approach allows applications to choose their own security models. High-value transactions can use conservative, multi-layered security approaches like Multisig ISMs or Aggregation ISMs, while low-value operations can use faster, more cost-effective verification methods like Optimistic ISMs. This modular security approach prevents bridge exploits by allowing customized security models that enhance bridge security.
Decentralized Failure Domains
Traditional bridges create systemic risk through centralized validator sets. Unlike centralized bridge architectures that concentrate risk in single validator sets, Hyperlane distributes security responsibility across individual applications and chain developers. This approach prevents systemic failures and ensures that potential security issues remain isolated to specific implementations rather than affecting the entire ecosystem, significantly improving DeFi security.
The Challenge: $3.5B+ Lost to Bridge Exploits
The blockchain ecosystem has lost over $3.5 billion from bridge exploits as of 2025. Cross-chain infrastructure has historically suffered from significant security weaknesses that have resulted in substantial financial losses. Traditional bridge security models rely on centralized validator sets that create single points of failure, making them vulnerable to coordinated attacks and key compromise scenarios.
Critical Weaknesses in Legacy Systems:
Existing bridge architectures face several fundamental security challenges:
- Centralized Validation Points: Single validator sets create systemic risk where compromise of validator keys can result in complete bridge failure and asset loss
- Uniform Security Models: One-size-fits-all security approaches fail to account for varying risk profiles across different applications and use cases
- Permissioned Deployment Barriers: Centralized governance creates bottlenecks that slow innovation and limit the scalability of cross-chain applications
- Limited Customization Options: Rigid security frameworks prevent applications from implementing security measures appropriate to their specific requirements
Hyperlane addresses these fundamental issues through its permissionless bridges deployment model and modular security architecture, providing developers with the tools needed to build secure, resilient cross-chain applications. This approach prevents bridge exploits and enhances DeFi security across the entire ecosystem.
Interchain Security Modules (ISMs): Customizable Security for Every Application
Interchain Security Modules (ISMs) are Hyperlane's core innovation in cross-chain security. These smart contracts operate on destination chains and verify the legitimacy of incoming cross-chain messages. Unlike traditional bridges that use uniform security models, ISM modules let applications customize their security requirements based on specific risk profiles. The Interchain Security Modules framework provides granular control over protection mechanisms.
- Multisignature ISM: Implements a configurable threshold signature scheme requiring multiple independent validators to cryptographically verify message authenticity. This approach prevents single-point-of-failure scenarios by requiring simultaneous compromise of multiple validator keys, significantly enhancing security for high-value transactions.
- Aggregation ISM: Combines multiple independent security mechanisms operating in parallel. This defense-in-depth strategy requires verification from several different ISM types simultaneously, creating redundant security layers that prevent failure of any single security model from compromising message integrity.
- Optimistic ISM: Employs an optimistic verification model with community-monitored challenge periods. Messages are initially accepted and processed, with designated watchers able to submit cryptographic fraud proofs during configurable time windows to revert malicious transactions, balancing security with operational efficiency.
- Rollup Integration ISM: Leverages native rollup security mechanisms by integrating directly with underlying blockchain fraud and validity proof systems. This approach eliminates redundant security layers by utilizing the rollup's inherent security guarantees, optimizing both security and performance.
This modular security architecture enables Hyperlane applications to implement precisely the level of protection required for their specific use cases, from high-security financial transactions to cost-optimized low-value operations.
Key Advantages: Why Developers Choose Hyperlane
Hyperlane development offers several compelling advantages that distinguish it from alternative interoperability solutions:
Security and Flexibility
- Permissionless Architecture: Deploy cross-chain messaging infrastructure on any blockchain without requiring approval or permission from centralized authorities
- Modular Security Design: Customize security requirements through Interchain Security Modules that match your application's specific risk profile and operational needs
- Distributed Risk Management: Security responsibility is distributed across applications, preventing systemic failures from centralized validator set compromises
- Open Source Foundation: Fully auditable codebase with transparent security mechanisms that enable community verification and continuous improvement
Performance and Reliability
- Flexible Security Models: Choose security approaches that balance speed, cost, and protection based on your specific application requirements
- Economic Security Mechanisms: Verifiable fraud proofs and economic slashing mechanisms align validator incentives with protocol security, ensuring honest behavior
- Replay Attack Prevention: Globally unique message identifiers prevent double-spending and replay attacks, ensuring message integrity across all transactions
- Security-Agnostic Relayers: Relayer infrastructure cannot manipulate message content, ensuring security remains entirely within the ISM framework
Economic and Technical Safeguards: Multi-Layered Protection
Hyperlane security implements multiple layers of economic and technical safeguards designed to prevent fraud and malicious attacks. The modular security approach ensures that bridge security is maintained through comprehensive protection mechanisms. These safeguards work in concert to ensure the security and integrity of cross-chain security communications while maintaining operational efficiency and preventing bridge exploits.
Key protection mechanisms include:
- Verifiable Fraud Proofs: Designated watchtowers can submit cryptographically verifiable fraud proofs that trigger automatic slashing of validator staked assets, creating strong economic incentives for honest behavior and preventing malicious message attestations
- Economic Slashing: Validators must stake substantial collateral, and fraudulent message attestations result in automatic slashing, aligning economic incentives with protocol security and ensuring validator accountability
- Replay Attack Protection: The Mailbox contract prevents replay attacks through globally unique message identifiers and complete delivery history mapping, ensuring each message can only be executed once and preventing double-spending scenarios
- Security-Agnostic Relayers: Relayer agents function purely as message delivery mechanisms without security privileges, removing relayers as potential central attack points and ensuring security remains entirely within the ISM framework
Hyperlane protection ensures the security of cross-chain operations through these comprehensive safeguards that prevent exploits and maintain the integrity of the interoperability framework.
Future Development: Expanding Hyperlane Capabilities
The Hyperlane platform continues to evolve with ongoing innovations and expansions:
Ongoing Enhancements
- Expanded ISM Types: Developing additional Interchain Security Module variants to support broader use cases and security models, enabling more sophisticated protection mechanisms
- Enhanced Validator Networks: Growing the decentralized validator ecosystem through partnerships with restaking protocols and validator networks, increasing security and decentralization
- Developer Tooling: Comprehensive SDKs and documentation improvements to simplify integration and accelerate development of cross-chain applications
- Cross-Chain Applications: Supporting additional applications and use cases across the multichain ecosystem, expanding the platform's utility and adoption
- Security Research: Continuous security audits and research initiatives to identify and prevent new attack vectors, ensuring long-term platform security
Community and Support
Hyperlane community maintains active engagement through regular updates, transparent communication, and comprehensive documentation. Developers can connect with the team via Discord, GitHub, and Twitter for assistance with integration, security questions, and best practices.
Hyperlane vs. Alternative Solutions: Distinctive Advantages
While multiple platforms offer cross-chain bridging services, Hyperlane technology distinguishes itself through unique architectural advantages:
Permissionless Deployment
Unlike competitors requiring centralized approval, Hyperlane infrastructure enables permissionless deployment of cross-chain messaging on any blockchain, creating truly decentralized interoperability without gatekeepers or governance bottlenecks.
Modular Security Architecture
Our ISM framework allows applications to customize security requirements, preventing the systemic failures that have caused significant losses across traditional monolithic bridge designs while providing flexibility for diverse use cases.
Distributed Failure Domains
Hyperlane security distributes security responsibility across applications rather than relying on centralized validator sets, preventing systemic risk and reducing vulnerability to coordinated attacks.
Getting Started: Building Secure Cross-Chain Applications
Ready to build secure cross-chain applications? Here's how to begin with Hyperlane:
For Developers: Deploy Hyperlane's Mailbox contract on your target blockchain, configure your Interchain Security Modules (ISMs) based on your security requirements, and start sending cross-chain messages. The permissionless architecture means no approval is needed—you can begin immediately.
For Applications: Integrate Hyperlane's SDK into your application, choose the appropriate ISM for your use case (Multisig for high-value transactions, Optimistic for low-value operations), and begin secure cross-chain communication with minimal setup overhead.
For Validators: Join Hyperlane's decentralized validator network by staking collateral and running validator nodes. Earn rewards while helping secure the cross-chain ecosystem and contributing to decentralized infrastructure.
Security Best Practices for Hyperlane Developers
While Hyperlane framework implements multiple security layers, developers should follow these best practices:
- Always verify you're using the official Hyperlane contracts from the verified GitHub repository to prevent malicious code execution
- Choose appropriate ISMs based on your application's value and risk profile, balancing security requirements with operational efficiency
- Conduct thorough security audits before deploying production applications to identify potential vulnerabilities
- Monitor validator sets and ensure sufficient decentralization to prevent centralization risks
- Implement proper error handling and fraud proof mechanisms to ensure robust application behavior
- Stay updated with Hyperlane security announcements and best practices to maintain optimal security posture
Conclusion: Why Hyperlane is the Ultimate Cross-Chain Security Solution
Hyperlane has established itself as the definitive platform for secure blockchain interoperability. With revolutionary permissionless bridges deployment, modular security architecture, and unwavering commitment to preventing bridge exploits, Hyperlane represents the future of secure multichain communication. The platform's Interchain Security Modules (ISMs) provide unparalleled bridge security and cross-chain security capabilities.
Whether you're building cross-chain applications, deploying on new blockchains, or securing high-value transactions, Hyperlane provides the most flexible, secure, and decentralized solution available today. The modular security ISM framework allows you to customize security to match your needs while preventing the systemic vulnerabilities that have plagued traditional bridges. This approach significantly enhances DeFi security across the entire ecosystem.
Join the growing ecosystem of developers and applications that trust Hyperlane for their cross-chain infrastructure needs. Experience the next generation of blockchain interoperability with permissionless bridges, modular security, and protection against $3.5B+ in bridge exploits.